Network Protection
Protection Framework
- Traffic Analysis#Firewall
- Form a barrier through which the traffic going in each direction must pass.
- Traffic Analysis#Intrusion Detection System
- Detect unusual patterns of activity or patterns of activity that are known to correlate with intrusions.
- Traffic Analysis#Intrusion Prevention System
- An extension of IDS to attempt to block or prevent detected malicious activity.
- Honeypot
- 可以引诱潜在攻击者远离关键系统,同时收集攻击者的攻击信息
- Honeywords
- 使用虚假的 Password,以获取尝试盗取账号的恶意攻击者的相关信息
Load Balancing
- To defence DDoS Attack
- Methods
- Least Connection Method: 优先选择当前服务连接最少的服务器
- Least Response Time Method: 优先选择响应时间最短的服务器
- Round Robin Method: 轮询调度
- IP Hash: 根据 IP 的 hash 值选择对应的服务器
Traffic Scrubbing
- 定义:提供数据清理服务,用于分析流量并过滤恶意的流量
- 使用方式:一旦检测到攻击,将流量重定向到流量重定向到洗刷服务
- 验证方式:自己构建攻击,以检验实用性
User Authentication
- Means of Authentication
- Information the user knows: password
- Information the user possesses: phone, card
- Information the user is(static biometrics): fingerprint, face
- Information the user does(dynamic biometrics): voice pattern, handwriting characteristics
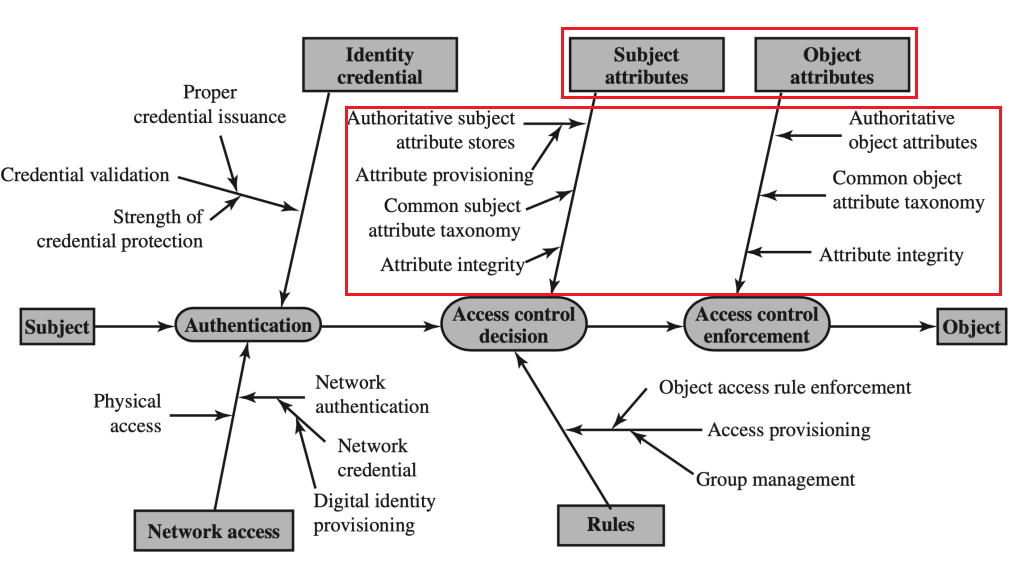
Password with salt
- Salt Purpose:防止相同密码的哈希值也相同
- 增大离线字典攻击的难度
- 增大判断用户使用相同密码的难度
- Register a new password
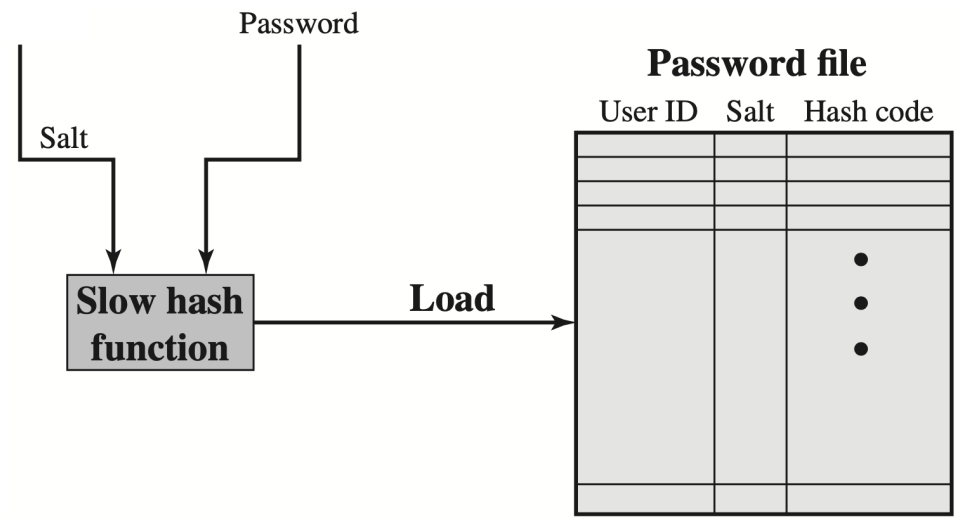
- Verify a password
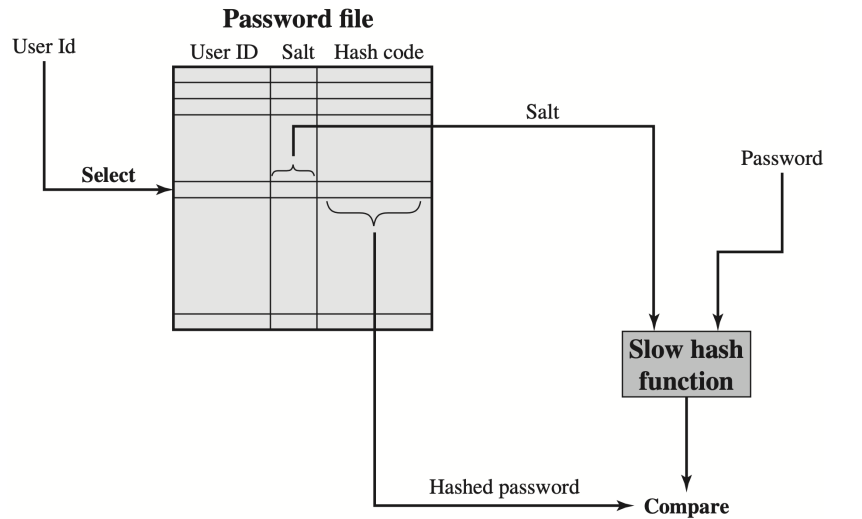
Token
| Card Type | Defining Teature | Example |
|---|---|---|
| Embossed | Raised characters only, on front | Old credit card |
| Magnetic stripe | Magnetic bar on back, characters on front | Bank card |
| Memory | Electronic memory inside | Prepaid phone card |
| Smart Contact/Contactless | Electronic memory and processor inside | Biometric ID card |
Biometric
- Some physical characteristics
- facial characteristics 面部特征
- fingerprints 指纹
- hand geometry 掌纹
- retinal pattern 视网膜
- iris 虹膜
- signature 签名
- voice 声纹
- Enrollment and Verification
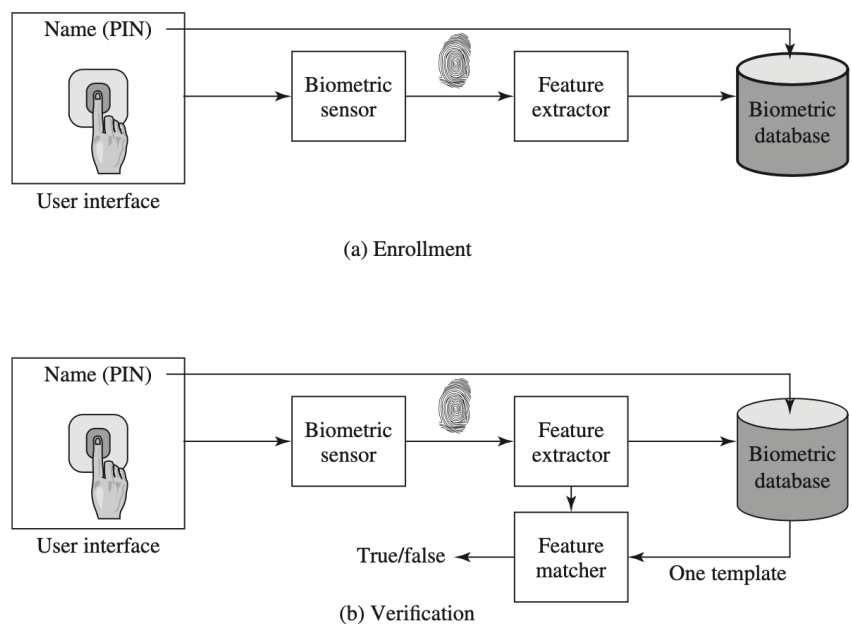
- False Match Rate
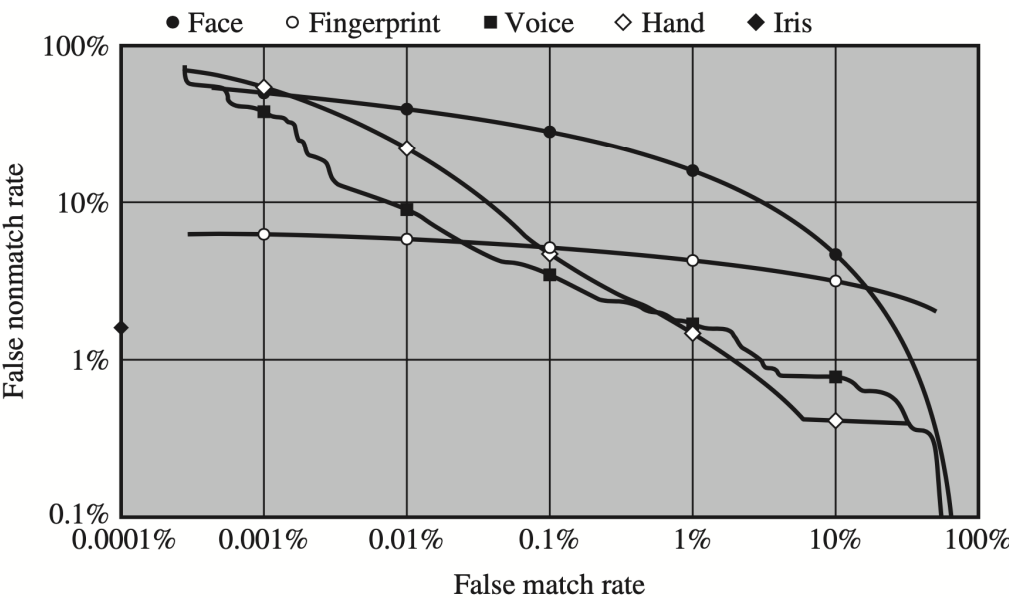
Attack and Defense
| Attacks | Athenticators | Examples | Typical Defenses |
|---|---|---|---|
| Client Attack | Password | Guessing, exhaustive search | Large entropy; limited attempts |
| Client Attack | Token | Exhaustive search | Same as password; theft of object requires presence |
| Client Attack | Biometric | False match | Same as password |
| Host Attack | Password | Plaintext theft, dictionary/exhaustive search | Hashing; large entropy; protection of password database |
| Host Attack | Token | Passcode theft | Same as password; 1-time passcode |
| Host Attack | Biometric | Template theft | Capture device authentication; challenge response |
| Eavesdropping, theft, and copying | Password | Shoulder surfing | User diligence to keep secret; administrator diligence to quickly revoke compromised passwords; multifactor authentication |
| Eavesdropping, theft, and copying | Token | Theft, counterfeiting hardware | Multifactor authentication; tamper resistant/evident token |
| Eavesdropping, theft, and copying | Biometric | Copying biometric | Copy detection at capture device and capture device authentication |
| Replay | Password | Replay stolen password response | Challenge-response protocol |
| Replay | Token | Replay stolen passcode response | Challenge-response protocol; 1-time passcode |
| Replay | Biometric | Replay stolen biometric template response | Copy detection at capture device and capture device authentication via chanllenge-response protocol |
| Torjan horse | Password, token, biometric | Installation of rogue client or capture device | Authentication of clinet or capture device within trusted security perimeter |
| Denial of service | Password, token, biometric | Lockout by multiple failed authentications | Multifactor with token |
Acccess Control
- Elements
- Subject: Entity capable of accessing objects
- Object: Resource to which access is controlled
- Access Right: Describe the way in which a subject may access an object
DAC - Discretionary Access Control
- 每个用户都有一套权限,定义他们对资源的访问级别。
Access Matrix
- 占用空间大,效率较高
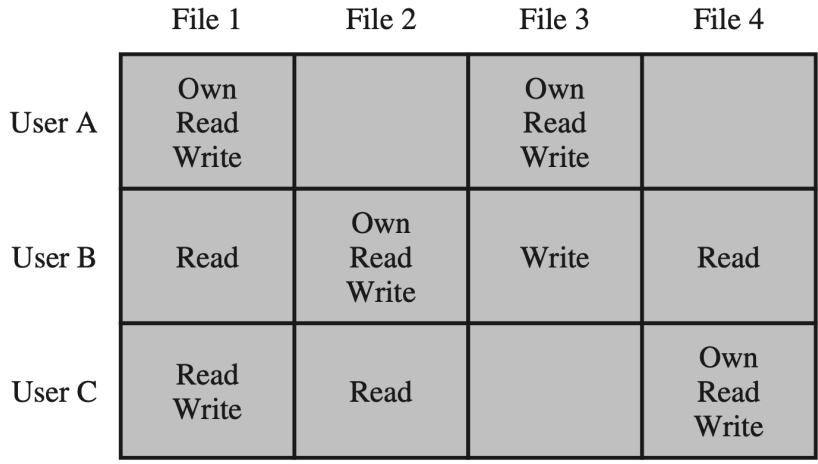
ACL: Access Control List
- 占用空间小,效率较低
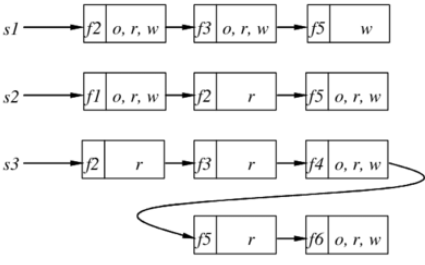
- Capability List
RBAC - Role-Based Access Control
- 早期访问控制技术#基于角色的访问控制模型 (RBAC)
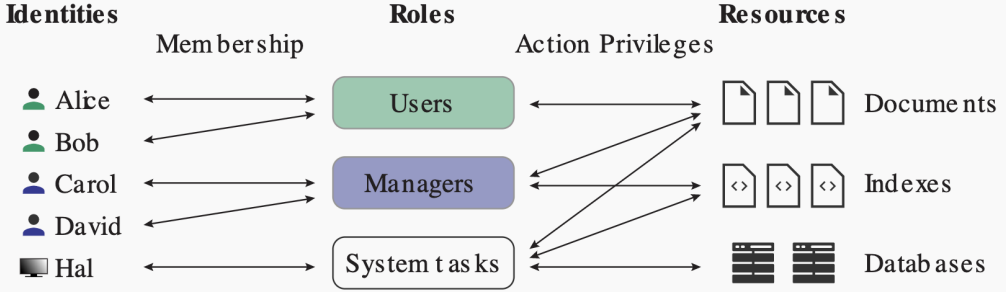
- 相较于 ABRC 效率较低
ABAC - Attribute-Based Access Control
Incident Response
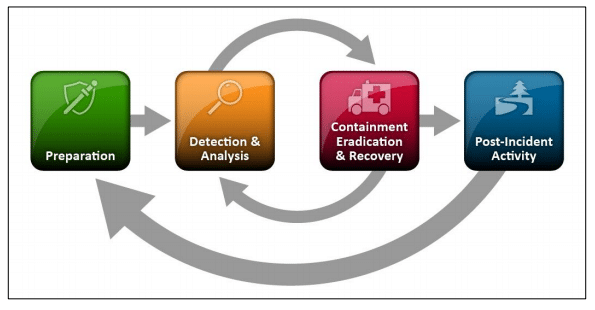
- Preparation
- 设置白名单 / 黑名单
- Detection & Analysis
- 检测潜在的攻击
- Containment Eradication & Recovery
- 阻止攻击网络,识别并阻塞攻击源
- Post-Incident Activity
- 恢复正常运转